PIA employs RAM-only servers, which means info is routinely deleted and challenging to steal. And so much, the U.
S. governing administration has not been equipped to power PIA to violate its no-logs coverage. This is simply because of U.
S. consumer protection rules, according to PIA. But even even though it hasn’t happened but, that will not necessarily mean PIA can’t eventually be pressured to breach its possess procedures.
- What are the VPNs for remote control do the trick?
- Are there any VPNs which offer an absolutely free free trial?
- Do VPNs help speech assistants like Alexa?
- Am I Able To try a VPN using a common public home pc?
- Can a VPN reduce the chances of identity theft?
- Could I try a VPN for obtain communication with medical solutions?
- Precisely what is a VPN for being able to access labeled information and facts?
- What are the VPNs for opening authorities internet websites?
Are there VPNs for whistleblowers?
The principal actuality pointing to this chance is that Non-public World-wide-web Access is U. S. -based mostly.
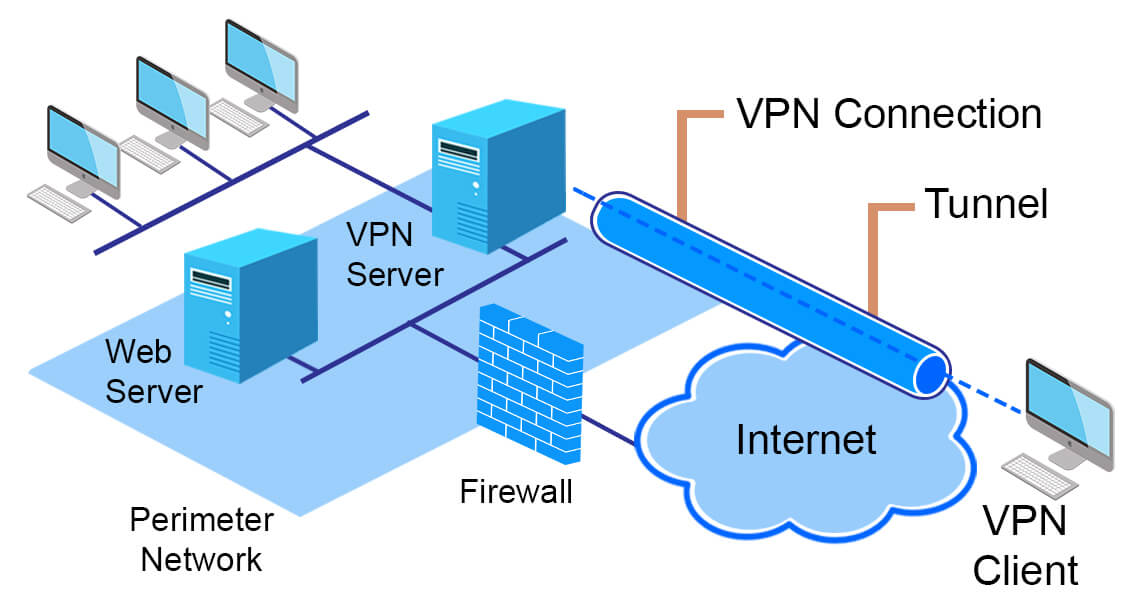
And the U. S. is portion of the 5 Eyes, Nine Eyes, and 14 Eyes Alliances, which are world networks associated in mass surveillance, including inside of their own nations around the world.
PIA has accomplished an exceptional work so far with its privateness initiatives, and we hope it continues to do an excellent job. But becoming positioned in a state that is part of a international surveillance community mullvad could not be the finest point for protecting consumer privateness. Note that Non-public Internet Entry was acquired by Kape Systems in 2019. Kape Systems owns other VPNs, including ExpressVPN, CyberGhost, and ZenMate VPN.
All VPNs under the Kape brand are thought to run independently of each individual other. Learn a lot more in our ExpressVPN critique . Kill switch.
PIA VPN supplies a get rid of change function positioned in the Privateness area of the application settings. A VPN get rid of switch is built to prevent information leaks from occurring if your safe link is interrupted. You can pick concerning two distinct get rid of change options:VPN Destroy Switch: Your basic kill switch that helps prevent leaks by blocking your net targeted visitors from going outside the house the VPN, like during an interrupted link. Sophisticated Destroy Swap: Blocks all web targeted traffic except you are related to the VPN.
If you want to take a look at the kill swap to see if it is really performing, the least difficult way is possibly turning on the State-of-the-art Eliminate Switch. This characteristic will make it so you won’t be able to access the web at all if you are not linked to the VPN. We examined this by turning on the aspect, disconnecting the VPN, and making an attempt to join to a web site applying Chrome. We were not able to join to anything online even even though our net relationship was continue to there. It’s secure to say, the eliminate swap works. Split tunneling.
Split tunneling is a feature that permits you to bypass the secure VPN connection with specific apps and IP addresses. PIA delivers this feature in the app configurations on the Split Tunnel tab. You may use split tunneling if you will not want an app to be slowed down by a VPN and you usually are not worried about stability or privacy inside that app. For case in point, you could let an on the internet video clip activity to bypass the VPN connection so you can keep rapid speeds although gaming.
In the meantime, your other on the web routines continue being personal and protected. Encryption. PIA allows you pick concerning AES-128 or AES-256 encryption. These are some of the strongest encryption algorithms out there and are extensively employed by corporations worldwide. You can find the encryption selections in the Protocols tab of the app settings within just the OpenVPN protocol portion. VPN protocol. PIA offers a number of VPN protocols to assist guarantee your protection whilst keeping substantial stages of transparency. This incorporates the open-source WireGuard and OpenVPN protocols, as properly as IKEv2/IPsec. You can locate the obtainable protocols in your application configurations in the Protocols tab. Note that Personal Internet Access with OpenVPN and WireGuard were the only readily available solutions we noticed on the Home windows desktop application. But we did see all three protocols, which include IKEv2/IPsec, have been offered in the iOS app. Identity Guard. PIA Id Guard is a characteristic that can enable you see no matter if an electronic mail address has been aspect of a data breach. We discovered this function in our on-line account working with a Chrome browser. Selecting the Identity Guard tab delivers you to a breach monitoring web site on the PIA site. Listed here, you can enter an e mail handle and PIA will check out to see irrespective of whether it truly is been uncovered. We entered a single of our junk e-mails (an electronic mail we use to indication up for all varieties of solutions and subscriptions) to see what would pop up.
